Enabling Secure Remote Access to OSCAR
Documentation Copyright [c] [y] by Adrian Starzynski under the Creative Commons Attribution-Share Alike 3.0 Unported License
Preface
Disclaimer: This article aims to provide guidance/tips on different remote access alternatives other than VPN. Everyone is responsible for ensuring their own regulatory/security compliances etc.
A problem with enabling WAN access (port forwarding) to OSCAR directly is that your OSCAR URL becomes a webpage that anyone can attempt to log in to from anywhere in the world (not secure and vulnerable to DDoS/brute force attacks).
A common solution to this is keeping WAN access to OSCAR disabled and using a VPN to access the clinic’s network to access your OSCAR. However, VPNs come with their own limitations and inconveniences, i.e. there must be a VPN server installed on-prem, the client accessing the network must have a VPN client installed on their device (which requires updates, setup for each new device you want to use VPN on), and if there are many doctors or users trying to use the VPN at the same time to access your OSCAR there will be a noticeable network slow-down.
This article aims to provide details on configuring Cloudflare Zero Trust for remote access to your OSCAR server, and some details on setting up a VPN access.
Remote Access Using Conventional VPN
If the OSCAR server is at an office with a solid firewall that has options for configuring VPN, such as a pfSense/Netgate/FortiGate/Cisco/PaloAlto, then there are a few options on setting up remote client access to the network.
There are 4 popular methods for setting up client remote access to a network:
- OpenVPN
- SSL-VPN
- WireGuard VPN
- L2TP (IPSEC) – less secure
Each firewall model has different configurations/supported protocols. OpenVPN, WireGuard and SSL-VPN protocols require the client to install an application to setup VPN. The application then prompts the user for a certificate or username/password authentication or single-sign-on depending on what is configured on the firewall. Windows and Mac have a built-in L2TP VPN client into the system network settings which can be used to configure VPN without additional applications.
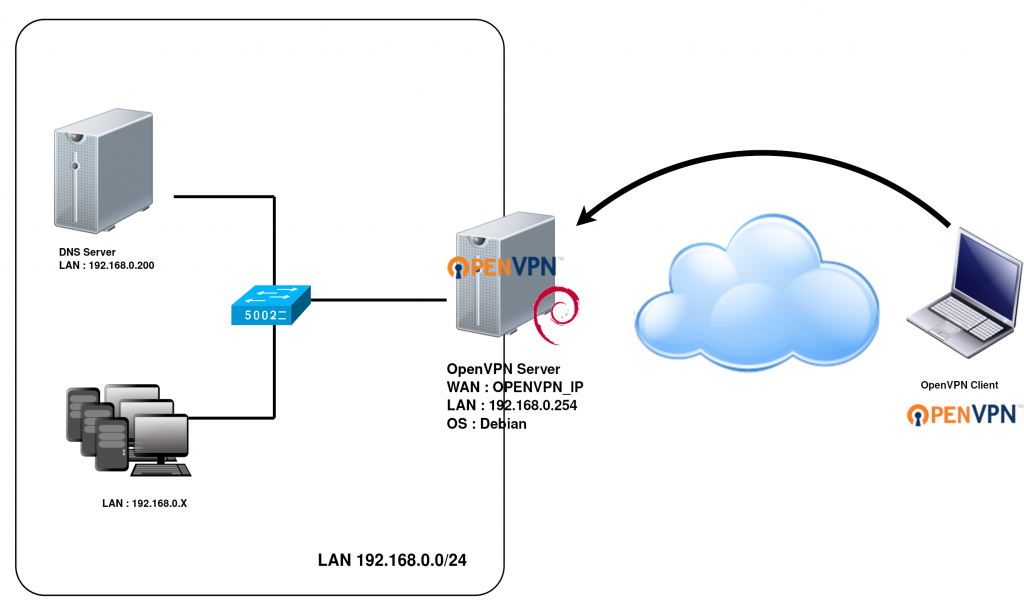
OpenVPN and WireGuard are open-source. If your firewall doesn’t include a built-in VPN server, you can install OpenVPN or WireGuard on a computer (i.e. a Raspberry Pi, or even the same server you use for OSCAR but that is not recommended due to security reasons) and forward the VPN port from your firewall to this device that will run the VPN server and allow connections into your network.
The most secure VPN access method is one which requires MFA in order to login to the VPN. L2TP does not support this.
If you are setting up VPN for users accessing OSCAR and OSCAR is the only resource that the users will be accessing on the network, then create a firewall rule to only allow the VPN tunnel to access the OSCAR server’s IP address. That way they pose less of a security threat as the whole network isn’t totally exposed in case a user leaks their VPN login or gets compromised.
Advanced firewalls such as FortiGate support single-sign-on configuration for SSL-VPN so that users can install the FortiClient application and use configured SAML 2.0 SSO (i.e. AzureAD, DUO, etc.) to sign into the VPN.
Advanced firewalls also usually allow purchasing a license for “ZTNA” (Zero Trust Network Access), which is a more secure method of granting access to the network. An example setup of this would be a FortiGate firewall connected to a FortiEMS (Fortinet Endpoint Management Server) or PaloAlto Network’s PrismaAccess, which support creating policies to only allow VPN access if the user has an updated operating system (i.e. Windows with latest security patches), a specific antivirus software, and inputs a MFA code.
ZTNA also re-authenticates the user. Conventional VPN’s function in a way that once the user logs in to the VPN, the door is “wide open” for them and there is no more traffic inspection/filtering done to ensure security as they have already logged in. ZTNA principle requires that all the traffic even after authenticating into the VPN must be filtered and the user is only allowed access to the resources they need (i.e. only the OSCAR EMR server and not all the other servers/devices on the network).
To add to the complexity of VPN options, there are some “client VPN connector” options such as OpenVPN Cloud which you install on a firewall that supports acting as a VPN Client (i.e. pfSense), meaning that the VPN server is in the cloud and your firewall acts as a client to connect the network to the server that is remote. Then devices authenticate to the VPN server that sits in the cloud, and their traffic is tunnelled down to the firewall. This is useful for some firewalls that support acting as a VPN client but not a VPN server.
Generally, setting up VPN access is complex at first and it is good to hire a network security professional to do it for you or check your configuration as a misconfigured VPN server can be a huge security vulnerability.
Remote Access using Cloudflare Zero Trust
Since 2020, there is a new solution to this on the market which works perfectly for clinics with up to 50 users for free – Cloudflare Zero Trust.
Cloudflare is a DNS and network services company with one of the world’s largest and fastest networks. They offer fast DNS, caching, security… solutions for any domain with a few plans available. The Cloudflare free plan includes everything you need to protect access to your OSCAR remotely as an alternative to VPN.
With Cloudflare Zero Trust, you map your domain’s NS records to Cloudflare’s name servers (they will show you the closest servers to you to use) and you can then set up protection of either an entire domain (i.e. myclinic.com), subdomain (test.myclinic.com), or directory (test.myclinic.com/thisfolder). By ‘protection’ I mean access control to that resource – yes it really is that simple.
The great thing about Cloudflare access is that you can enable access to services on your network without needing to forward any ports on your router or expose your machine. You just install the cloudflared service and setup a tunnel that connects directly to Cloudflare and then you can set a Cloudflare application access policy so that in order for people to access that domain they will need to authenticate (i.e. MFA, SSO, email code, etc.) You don’t need to have a static IP for this to work since it’s a service installed on any operating system that will run the Cloudflare tunnel connector. This way, there is no exposed public IP and everything is tunnelled through Cloudflare, so no need for a static IP or any DDNS provider etc.
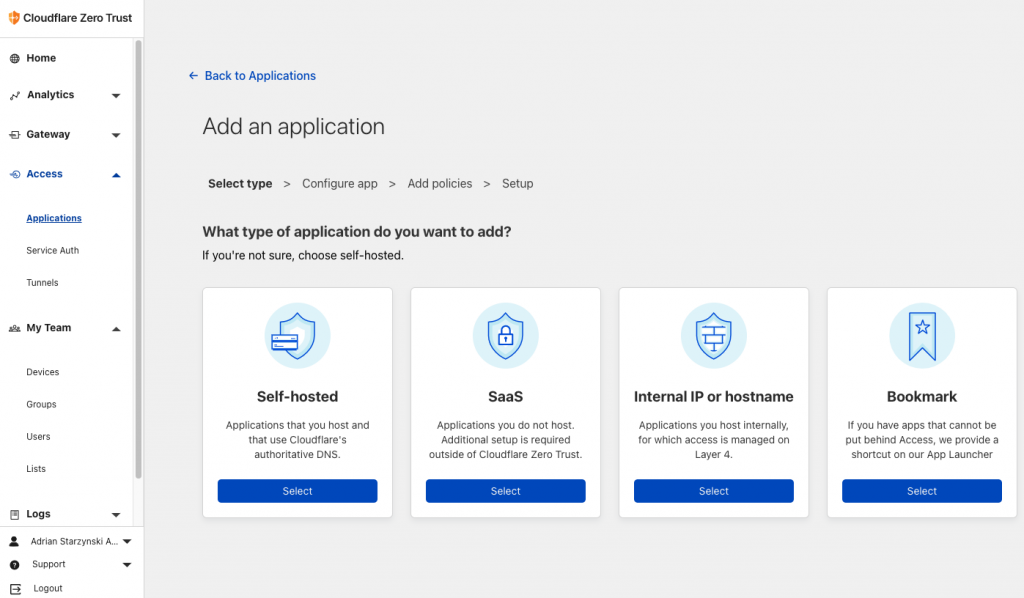
Step 1 – setup the Cloudflared tunnel connector service
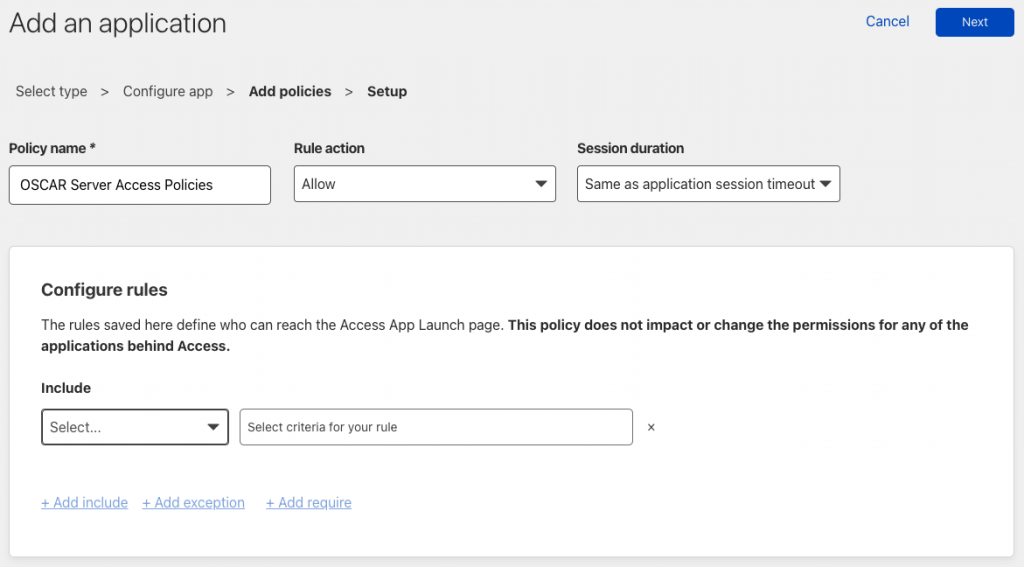
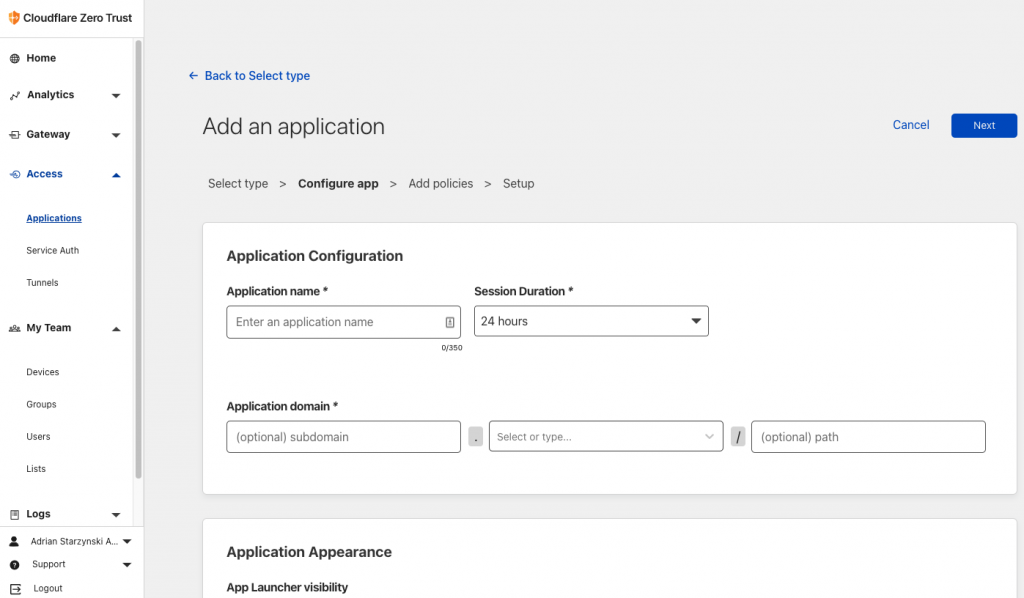
Step 2 – protect the application’s URL
(‘Application’ means the domain/subdomain where your OSCAR is located, i.e. oscar.myclinic.com or myclinic.com)
- Admin of Cloudflare Zero Trust will configure and enable login methods for access to the cloud-protected application (i.e. email OTP verification, SAML 2.0 SSO, or direct integration with AzureAD/Google Workspace/OneLogin/Okta etc. – they have dozens of methods available to configure)
- Admin will add an application for the domain/subdomain OSCAR is located at (i.e. myclinic.com) or subdomain (oscar.myclinic.com)
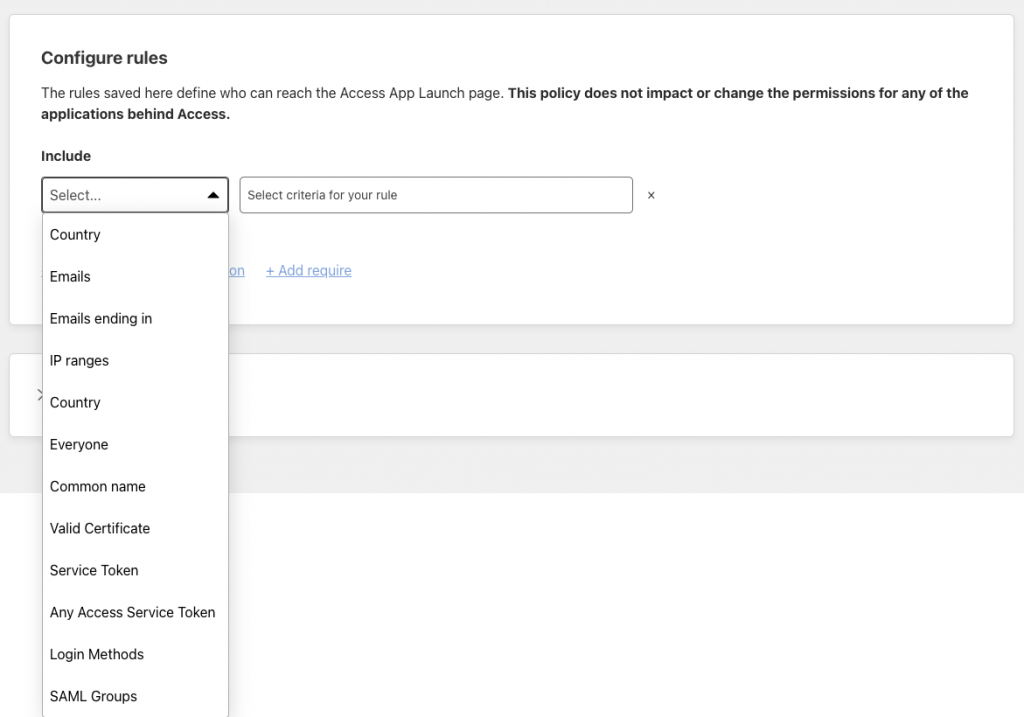
- Add an access policy to require certain authentication methods or only enable certain users to access the application, set certain IPs whitelisted so they don’t need authentication (i.e. the IP of an integration’s API server such as an online booking provider which is configured with OSCAR), and set a login session expiration period (i.e. 24 hrs, 1 week, etc.)
- Now the application is protected. This means that anyone who visits the address which you protected (i.e. myclinic.com, oscar.myclinic.com, myclinic.com/oscar) will be forced to authenticate via Cloudflare through the authentication method you setup. Once they authenticate successfully, they are granted access to the application for the period set in token expiration setting of Cloudflare.
Simple example of access workflow protected OSCAR application using Cloudflare Zero Trust:
- user visits your OSCAR URL i.e. oscar.myclinic.com
- user is forced to authenticate using the authentication method/provider you setup in Cloudflare Zero Trust admin panel
- once they authenticate, they are able to access OSCAR and they must login to OSCAR as usual
Advantages:
- no need for a VPN
- no need for VPN client updates, VPN server administration/security updates etc.
- users can access the OSCAR link remotely and authenticate with the clinic’s existing IdP (if any) or by other means of login (simplicity) – so no need to give them additional VPN access etc. (security)
- OSCAR runs faster through DNS-level domain/subdomain WAN access protection (the traffic doesn’t need to pass through a VPN)
- enforce multifactor authentication (security)
- restrict access to only OSCAR instead of having to give them VPN access to your whole network (most small-med business routers/VPN solutions don’t offer network endpoint restriction per user)
- access monitoring reports via Cloudflare
- DDoS protection, firewall (only authenticated users can access the OSCAR system which they still need to login to)
Author of this article recommends you review the below-linked article and video.
See Cloudflare’s blog article on Zero Trust here: The Zero Trust platform built for speed (cloudflare.com)
See Cloudflare’s video on Zero Trust here.
Documentation on Cloudflare Zero Trust
Cloudflare Zero Trust documentation · Cloudflare Zero Trust docs
Notes
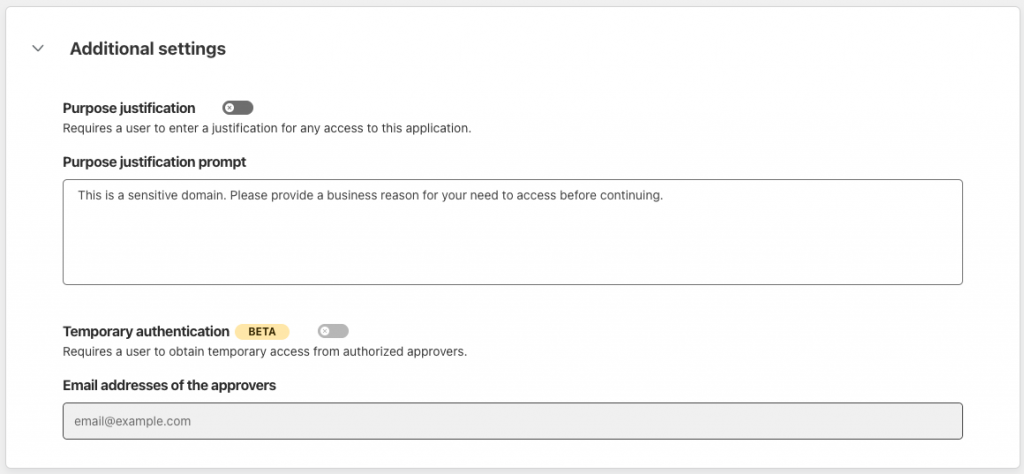
You can also make the users who are trying to access the application behind Cloudflare Access (your OSCAR sever) write a ‘justification’ before accessing it and you can set the justification to require approval. This may be useful if i.e. you don’t want MOAs logging in from home regularly so you allow them access in case there’s an emergency situation where they need to do something they forgot, for example, and they will need to write a justification message, and if you have approvals configured, then an approval request will be sent to X email address (i.e. clinic manager) who can approve the remote access request.
Screenshots of Cloudflare Configuration